Online privacy is a complicated issue. Thousands of companies are vying for your attention on the internet, and that means data about your habits and interests is extremely valuable. Many companies make a lot of money collecting and selling that data.
But not everyone is comfortable with that idea. It feels like an invasion of privacy.
Fortunately, there are a number of tools that can help protect your privacy online. TheBestVPN’s guide to online privacy contains an extensive discussion of these tools, but we’ve collected them here in a shortened format to give you a quick overview.
VPNs encrypt your web traffic so no one can see which sites you’re visiting or what you’re doing while you're there. This is the most crucial step in protecting your online privacy.

Note that free VPNs aren’t worth using because there’s a good chance they’re collecting and selling information on your browsing habits.
If you’re looking for a VPN, we recommend ExpressVPN for its security, ease of use, and affordability.
Modern browsers come with a built-in privacy protection mode called “incognito” or “privacy” mode. You can usually access this by hitting CTRL + SHIFT + N (or CMD + SHIFT + N on a Mac).
This mode prevents the browser from storing information about what you’re doing online. To be clear, however, this only prevents data from being stored on your computer. No one will be able to see what you were doing by looking at your browser history, but incognito mode doesn’t protect against snooping on your connection.
Companies use all sorts of tools that track you across the internet. Advertisers, social networks, and other organizations use small pieces of code to see where you go, and they use that information to show you ads they think will get you buy.
You can use tools like Ghostery and Disconnect to stop these activity trackers from monitoring your browsing habits.
Online ads are annoying—but they could also be a danger to your privacy. In addition to serving up ads that you probably don’t want to see, they track you across the web, just like the trackers we discussed above.
Malicious ads can also be used to infect your computer with malware.
All in all, it’s a good idea to block ads. An effective ad blocker prevents ads from being loaded in your browser, cleaning up your browsing experience and protecting your privacy. There are lots of great options; uBlock Origin is one of the best available. AdBlock Plus and AdBlock (which, despite the name, isn’t related to ABP) are also solid choices.
To prevent your emails and IMs from being snooped on or trawled for information, we recommend using a private messaging app that’s committed to privacy. Telegram is one of the best options for this; it does a great job of protecting your privacy and the app is free.
Telegram is available on mobile devices as well as desktop computers, which makes it a great tool for all-around messaging.
The popular messaging app WhatsApp also provides solid end-to-end encryption that protects the information in your messages. And it has the advantage of being extremely popular; there’s a chance that your family and friends are already using it.
You can think of HTTP as the language that the web speaks. It’s how information is transferred between you and the websites that you’re using. Unfortunately, HTTP isn’t secure. If someone manages to intercept your HTTP connection, they can see everything you’re doing.
HTTPS is a secure version of HTTP, and it encrypts your web traffic. This means that even if someone is able to intercept your traffic, they won’t be able to see what you’re doing.
You’ll know that you’re using HTTPS when you see something like this in your browser:
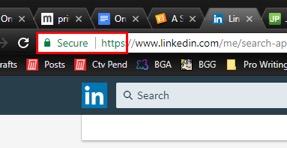
Unlike a VPN, someone snooping on your connection will still be able to see which websites you’re going to. So it’s not a replacement for your VPN. But if you can’t use a VPN, it’s a good second line of defense.
To make sure that you’re always using HTTPS when it’s available, download the Electronic Frontier Foundation’s HTTPS Everywhere extension.
Cookies are small text files that websites store on your computer. Many of them make browsing the internet more convenient; they let you stay logged into Facebook, for example, so you don’t have to log in when you head back to the site after closing the tab.
But they can also be used to track your activity. And for that reason, it’s a good idea to clear your cookies on occasion. Every browser has a slightly different method for getting rid of cookies. In most, you can press SHIFT + CTRL + DELETE (or SHIFT + CMD + DELETE) to open up the menu for deleting your browsing history.
Digital Trends also has a walkthrough of deleting cookies on all major browsers.
In addition to your browsing traffic, it’s possible that your email could be monitored, and that’s a major privacy and security risk. Fortunately, there are secure email options that prevent this.
Secure email is encrypted before being sent and only decrypted when it reaches your recipient’s inbox. Of course, this requires that the recipient is also using a secure email client. So the more people you convince to start using secure email, the better.
Both ProtonMail and Hushmail are long-standing options that have proven their security over the year.
Every app on your phone has certain permissions. A camera app has permission to access the camera, for example. Google Maps has access to your locations so it can tell you where you are and give you directions.
But many apps ask for permissions that they don’t need. They may record the phone numbers that you make calls to, for example. Others might access your microphone or your text messages.
You can revoke these permissions, and we encourage you to do so regularly. On iOS, go to Settings and scroll down until you start seeing app names. Tap an app to see its permissions and revoke any it doesn’t need.
On Android, go to Settings > Apps (or Application Manager), and select an app. Tap Permissions to see what it has access to.
It’s an unfortunate fact of life that older devices are less secure. As newer models get released, manufacturers are less likely to issue security fixes when vulnerabilities are found in older models.
Even though it’s expensive, it’s a good idea to upgrade your devices when they’re a couple generations old (the iPhone 5, for example, no longer receives updates).
You might think that deleting a file is simple; you hit Delete or drag it to the trash, and it’s gone. But it’s not that easy; many files live on your hard drive long after they’ve been deleted, and it’s possible for a motivated attacker to get them back. It’s not easy, but it can definitely be done.
Using a secure deletion feature in a file shredding app makes sure this doesn’t happen. On Windows, you can use Eraser, and on Mac, Dr. Cleaner. These apps ensure that your files are totally deleted from your hard drive and that no one can get them back.
(Just watch out for insecure disk-cleaning apps!)
You might not think twice about posting your vacation photos on Facebook—but nefarious characters can use this information to their advantage. Tweeting about how much you’re enjoying the beach in the Maldives can clue a potential burglar into the fact that you’re not home.
You don’t have to completely censor yourself on Facebook and Twitter. Just think twice about what you’re posting, and consider whether someone could use that information to harm you.
Windows 10 might be giving away a lot more information than you realize. Despite some criticism, Microsoft still gives Windows a lot of power to collect data on what you’re doing.
To boost Windows 10’s security, you’ll need to head to Settings > Privacy. From there, you can access a lot of settings screens that contain settings you might want to change. Browse around and check out the settings, or look at ZDNet’s guide to security Windows 10.
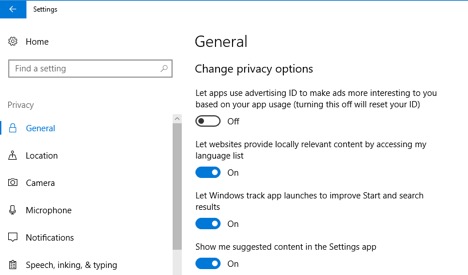
Of course, you can always get rid of Windows 10, too. Switching to a more secure operating system like Linux or macOS will solve these problems immediately. But it’s not always easy to make that change.
Google is the absolute king of online data collection. The amount of information they have about the world’s browsing habits is staggering. And while it’s impossible to completely escape them, you can make a few changes to minimize what they know about you.
The first and easiest method is to stop using Google to search. We recommend DuckDuckGo, a privacy-focused search engine that gets better all the time.

There are plenty of alternatives to Gmail, Google Drive, Google Plus, Google Hangouts, and most of Google’s other products as well. It’s just a matter of seeking them out. It might seem like a lot of effort, but remember that you’re fighting for your privacy.
There are lots of questionable stories about Facebook using smartphone microphones to listen in the background of conversations . . . but even beyond outlandish ideas like that, social media apps on your phone probably have a lot of permissions that they don’t need.
The fewer apps you have on your phone, the more secure and private your phone will be. You can always use your mobile browser to access your social media accounts instead of the apps.
It seems like every tech company has their own personal assistant now. Siri, Cortana, Google Assistant, Google Home, Alexa . . . they promise to make our lives easier by letting us say what we want and having them do it for us. And while they are very convenient, you may want to reconsider asking Siri all of your questions.
The things you say and ask are transmitted to the cloud, where they’re analyzed and an answer prepared. But providers are also analyzing what you’re asking about and using that information to tailor advertisements.
And some home assistants now come with cameras. Companies say that they won’t use those cameras for data collection, but do you trust them to live up to it? These are questions to keep in mind when you’re thinking about an Amazon Echo, Google smart-home device, or anything else that you can activate with your voice.
A virtual machine is basically a walled “sandbox” inside of your computer. Your computer simulates another computer and uses that second one to interface with apps. This keeps the apps from accessing the core of your machine, which can help keep it more secure.
While you probably don’t need to use a virtual machine for everything, it might be a good idea if you’re torrenting or downloading lots of files.
VirtualBox is one of the most popular methods for emulating another computer on your hard drive.
Public wifi is extremely convenient. But it can also be a significant privacy risk. Even if a public network is encrypted, there’s a chance that someone could be snooping on your traffic (this 7-year-old cracked a public hotspot in 11 minutes). And because wifi providers aren’t especially motivated to enhance their security, it could happen on almost any network.
No matter the level of security, it’s a good idea to avoid public wifi when you can. Use your phone’s data plan, or carry a mobile hotspot with you.
And if you do need to use public wifi, make sure not to access any important sites or type personal information like your credit card number of address. Using a VPN also adds another layer of protection to your device.
As you can see, protecting your privacy while you’re on the internet is a complicated issue. There are all sorts of things you can do to prevent snooping on your online activity, but most of them protect from specific things and leave you open to other attacks.
That’s why it’s a good idea to use multiple methods to secure your browsing. Use a VPN and a secure email app. Block ads and use Telegram to message your family and friends. Download a privacy extension for your browser and start using DuckDuckGo.
You may not want to go all the way to using Tor and securely deleting files, and that’s okay. But we strongly encourage you to take as many steps as possible to improve your privacy online.
Courtesy of John Mason,
Cyber Security/Privacy enthusiast
TheBestVPN.com
Additional Resources:
A Parent's Guide To Ensuring Their Children's Digital Privacy (masteroflegalstudies.com)
A Parents' Guide to Cyber Security (useful resources to help protect your family’s devices and networks)